Role Based Access Control
How RBAC Works
Define who can access what to who and which organization (project or domain) through SpaceONE's RBAC (Role Based Access Control).
For example, the Project Admin Role can inquire (Read) and make several changes (Update/Delete) on all resources within the specified Project. Domain Viewer Role can inquire (Read) all resources within the specified domain. Resources here include everything from users created within SpaceONE, Project/Project Groups, and individual cloud resources.
Every user has one or more roles, which can be assigned directly or inherited within a project. This makes it easy to manage user role management in complex project relationships.
Role defines what actions can be performed on the resource specified through Policy. Also, a Role is bound to each user. The diagram below shows the relationships between Users and Roles and Projects that make up RBAC.
This role management model is divided into three main components.
Role. It is a collection of access right policies that can be granted for each user. All roles must have one policy. For more detailed explanation, please refer to Understanding Role.
Project. The project or project group to which the permission is applied.
User. Users include users who log in to the console and use UI, API users, and SYSTEM users. Each user is connected to multiple Roles through the RoleBinding procedure. Through this, it is possible to access various resources of SpaceONE by receiving appropriate permissions.
Basic Concepts
When a user wants to access resources within an organization, the administrator grants each user a role of the target project or domain. SpaceONE Identity Service verifies the Role/Policy granted to each user to determine whether each user can access resources or not.
Resource
If a user wants to access a resource in a specific SpaceONE project, you can grant the user an appropriate role and then add it to the target project as a member to make it accessible. Examples of these resources are Server, Project, Alert .
In order to conveniently use the resources managed within SpaceONE for each service, we provide predefined Role/Policy. If you want to define your own access scope within the company, you can create a Custom Policy/Custom Role and apply it to the internal organization.
For a detailed explanation of this, refer to Understanding Role.
Policy
A policy is a collection of permissions. In permission, the allowed access range for each resource of Space One is defined. A policy can be assigned to each user through a role. Policies can be published on the Marketplace and be used by other users, or can be published privately for a specific domain.
This permission is expressed in the form below. {service}.{resource}.{verb} For example, it has the form inventory.Server.list .
Permission also corresponds to SpaceONE API Method. This is because each microservice in SpaceONE is closely related to each exposed API method. Therefore, when the user calls SpaceONE API Method, corresponding permission is required.
For example, if you want to call inventory.Server.list to see the server list of the Inventory service, you must have the corresponding inventory.Server.list permission included in your role.
Permission cannot be granted directly to a user. Instead, an appropriate set of permissions can be defined as a policy and assigned to a user through a role. For more information, refer to Understanding Policy.
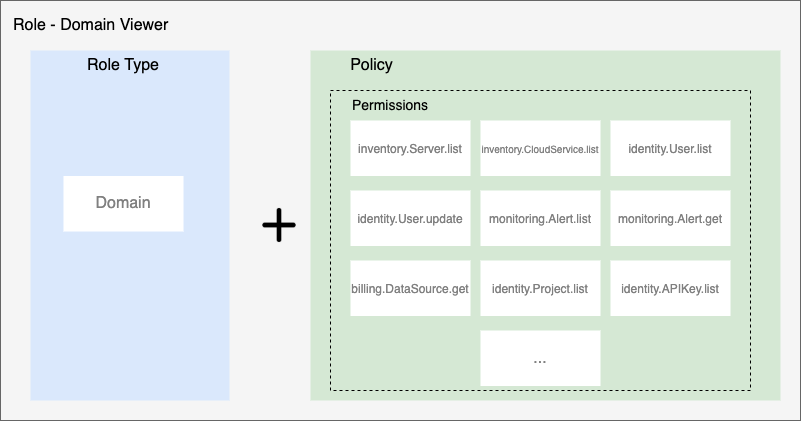
Roles
A role is composed of a combination of an access target and a policy. Permission cannot be directly granted to a user, but can be granted in the form of a role. Also, all resources in SpaceONE belong to Project. DOMAIN, PROJECT can be separated and managed.
For example, Domain Admin Role is provided for the full administrator of the domain, and Alert Manager Operator Role is provided for event management of Alert Manager.
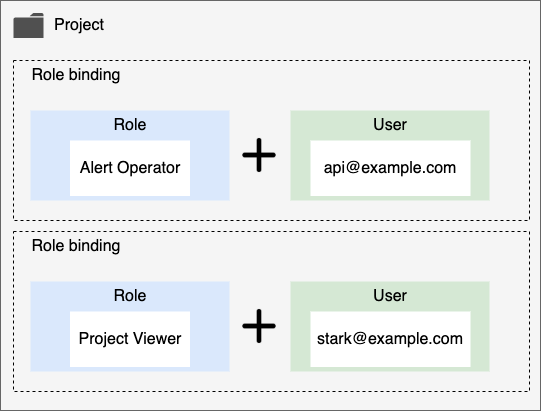
Members
All cloud resources managed within SpaceONE are managed in units of projects. Therefore, you can control access to resources by giving each user a role and adding them as project members.
Depending on the role type, the user can access all resources within the domain or the resources within the specified project.
- Domain: You can access all resources within the domain.
- Project: You can access the resources within the specified Project.
Project type users can access resources within the project by specifically being added as a member of the project.
If you add as member of Project Group, the right to access all subordinate project resources is inherited.
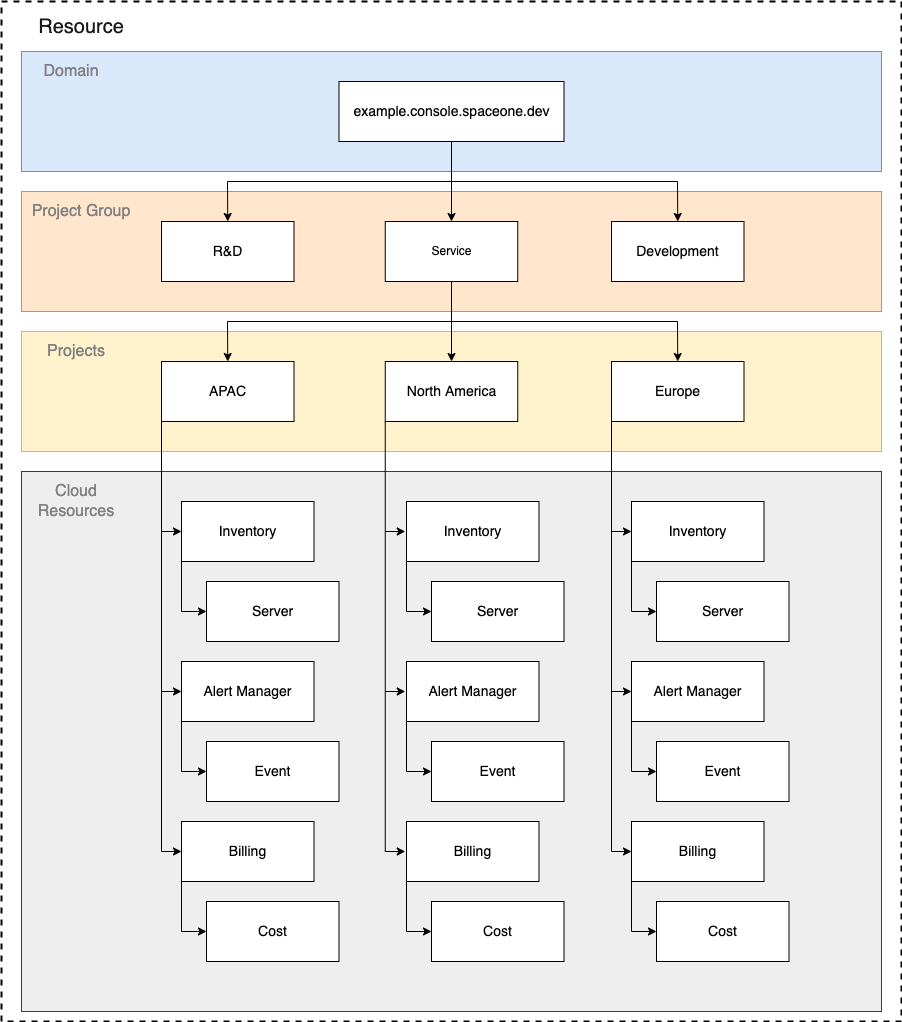
Organization
All resources in SpaceONE can be managed hierarchically through the following organizational structure.
All users can specify access targets in such a way that they are connected (RoleBinding) to the organization.
- Domain : This is the highest level organization. Covers all projects and project groups.
- PROJECT GROUP : This is an organization that can integrate and manage multiple projects.
- Projects : The smallest organizational unit in SpaceONE. All cloud resources belong to a project.