This the multi-page printable view of this section. Click here to print.
Configuration
1 - Set plugin certificate
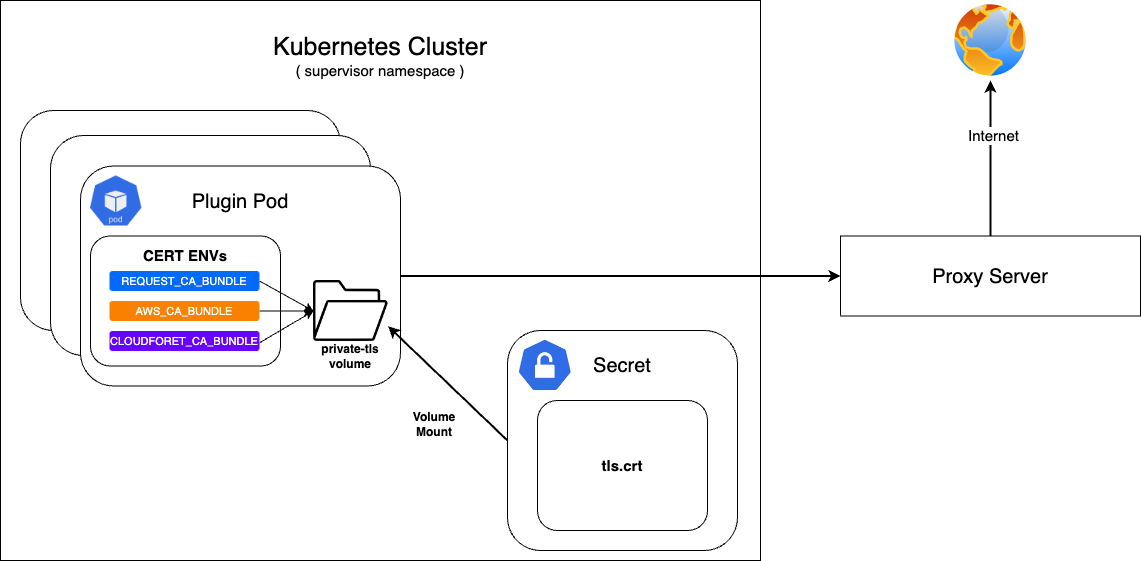
If Cloudforet is built in an on-premise environment, it can be accessed through a proxy server without direct communication with the Internet.
At this time, a private certificate is required when communicating with the proxy server.
First, configure the secret with the prepared private certificate and mount it on the private-tls volume.
After that, set the value of various environment variables required to set the certificate in supervisor's KubernetesConnectorto be the path of tls.crt in the private-tls volume.
Register the prepared private certificate as a Kubernetes Secret
| Parameter | Description | Default |
|---|---|---|
| apiVersion | API version of resource | v1 |
| kind | Kind of resource | Secret |
| metadata | Metadata of resource | {...} |
| metadata.name | Name of resource | private-tls |
| metadata.namespace | Namespace of resource | spaceone |
| data | Data of resource | tls.crt |
| type | Type of resource | kubernetes.io/tls |
kubectl apply -f create_tls_secret.yml
---
apiVersion: v1
kind: Secret
metadata:
name: spaceone-tls
namespace: spaceone
data:
tls.crt: base64 encoded cert # openssl base64 -in cert.pem -out cert.base64
type: kubernetes.io/tls
Set up on KubernetesConnector of supervisor
| Parameter | Description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor scheduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[] | Environment variables for plugin | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].name | Name of environment variable | REQUESTS_CA_BUNDLE, AWS_CA_BUNDLE, CLOUDFORET_CA_BUNDLE |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].value | Value of environment variable | /opt/ssl/cert/tls.crt |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[] | Volumes for plugin | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[].name | Name of volumes | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[].secret.secretName | Secret name of secret volume | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[] | Volume mounts of plugins | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].name | Name of volume mounts | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].mountPath | Path of volume mounts | /opt/ssl/cert/tls.crt |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].readOnly | Read permission on the mounted volume | true |
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
env:
- name: REQUESTS_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
- name: AWS_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
- name: CLOUDFORET_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
volumes:
- name: private-tls
secret:
secretName: private-tls
volumeMounts:
- name: private-tls
mountPath: /opt/ssl/cert/tls.crt
readOnly: true
Update
You can apply the changes through the helm upgrade command and by deleting the pods
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
2 - Change kubernetes namespace
When Cloudforet is installed in the K8S environment, the core service is installed in spaceone and the plugin service for extension function is installed in spaceone-plugin namespace. (In v1.11.5 and below, it is installed in root-supervisor.)
If the user wants to change the core service or plugin service to a namespace with a different name or to install in a single namespace, the namespace must be changed through options.
In order to change the namespace, you need to write changes in Cloudforet's values.yaml. Changes can be made to each core service and plugin service.
Change the namespace of the core service
To change the namespace of the core service, add the spaceone-namespace value by declaring global.namespace in the values.yaml file.
#console:
# production_json:
# CONSOLE_API:
# ENDPOINT: https://console.api.example.com # Change the endpoint
# CONSOLE_API_V2:
# ENDPOINT: https://console-v2.api.example.com # Change the endpoint
global:
namespace: spaceone-namespace # Change the namespace
shared_conf:
Change the namespace of plugin service
You can change the namespace of supervisor's plugin service as well as the core service. Life-cycle of plugin service is managed by supervisor, and plugin namespace setting is also set in supervisor.
Below is the part where supervisor is set to change the namespace of the plugin service in the values.yaml file. Add the plugin-namespace value to supervisor.application_scheduler.CONNECTORS.KubernetesConnector.namespace.
#console:
supervisor:
application_scheduler:
HOSTNAME: spaceone.svc.cluster.local # Change the hostname
CONNECTORS:
KubernetesConnector:
namespace: plugin-namespace # Change the namespace
Update
You can apply the changes through the helm upgrade command and by deleting the pods.
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
3 - Creating and applying kubernetes imagePullSecrets
Due to organization's security requirements, User can Build and utilize a private dedicated image registry to manage private images.
To pull container images from a private image registry, credentials are required. In Kubernetes, Secrets can be used to register such credentials with pods, enabling them to retrieve and pull private container images.
For more detailed information, please refer to the official documentation.
Creating a Secret for credentials.
Kubernetes pods can pull private container images using a Secret of type kubernetes.io/dockerconfigjson.
To do this, create a secret for credentials based on registry credentials.
kubectl create secret docker-registry my-credential --docker-server=<your-registry-server> --docker-username=<your-name> --docker-password=<your-pword> --docker-email=<your-email>
Mount the credentials Secret to a Pod.
You can specify imagePullSecrets in the helm chart values of Cloudforet to mount the credentials Secret to the pods.
WARN: Kubernetes Secret is namespace-scoped resources, so they need to exist in the same namespace.
Set imagePullSecrets configuration for the core service
| Parameter | description | Default |
|---|---|---|
| [services].imagePullSecrets[]] | imagePullSecrets configuration(* Each micro service section) | [] |
| [services].imagePullSecrets[].name | Name of secret type of kubernetes.io/dockerconfigjson | "" |
console:
enable: true
image:
name: spaceone/console
version: x.y.z
imagePullSecrets:
- name: my-credential
console-api:
enable: true
image:
name: spaceone/console-api
version: x.y.z
imagePullSecrets:
- name: my-credential
(...)
Set imagePullSecrets configuration for the plugin
| Parameter | description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor scheduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.imagePullSecrets[] | imagePullSecrets configuration for plugin | [] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.imagePullSecrets[].name | Name of secret type of kubernetes.io/dockerconfigjson for plugin | "" |
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
imagePullSecrets:
- name: my-credential
Update
You can apply the changes through the helm upgrade command and by deleting the pods
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
4 - Setting up http proxy
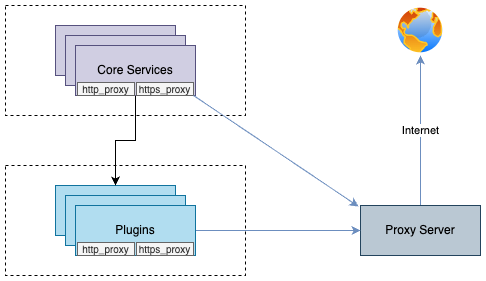
You can enable communication from pods to the external world through a proxy server by declaring the http_proxy and https_proxy environment variables.
This configuration is done by declaring http_proxy and https_proxy in the environment variables of each container.
no_proxyenvironment variable is used to exclude destinations from proxy communication.
For Cloudforet, It is recommended to exclude the service domains within the cluster for communication between micro services.
Example
Set roxy configuration for the core service
| Parameter | description | Default |
|---|---|---|
| global.common_env[] | Environment Variable for all micro services | [] |
| global.common_env[].name | Name of environment variable | "" |
| global.common_env[].value | Value of environment variable | "" |
global:
common_env:
- name: HTTP_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: HTTPS_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: no_proxy
value: .svc.cluster.local,localhost,{cluster_ip},board,config,console,console-api,console-api-v2,cost-analysis,dashboard,docs,file-manager,identity,inventory,marketplace-assets,monitoring,notification,plugin,repository,secret,statistics,supervisor
Set proxy configuration for the plugin
| Parameter | description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor schduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[] | Environment Variable for plugin | [] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].name | Name of environment variable | "" |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].value | Name of environment variable | "" |
WRAN:
Depending on your the installation environment, the default local domain may differ, so you need to change the default local domain such as.svc.cluster.localto match your environment. You can check the current cluster DNS settings with the following command.kubectl run -it --rm busybox --image=busybox --restart=Never -- cat /etc/resolv.conf
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
env:
- name: HTTP_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: HTTPS_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: no_proxy
value: .svc.cluster.local,localhost,{cluster_ip},board,config,console,console-api,console-api-v2,cost-analysis,dashboard,docs,file-manager,identity,inventory,marketplace-assets,monitoring,notification,plugin,repository,secret,statistics,supervisor
Update
You can apply the changes through the helm upgrade command and by deleting the pods
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
5 - Support private image registry
In organizations operating in an on-premise environment, there are cases where they establish and operate their own container registry within the internal network due to security concerns.
In such environments, when installing Cloudforet, access to external networks is restricted, requiring the preparation of images from Dockerhub and syncing them to their own container registry.
To automate the synchronization of container images in such scenarios, Cloudforet proposes using a Container Registry Sync tool called 'dregsy' to periodically sync container images.
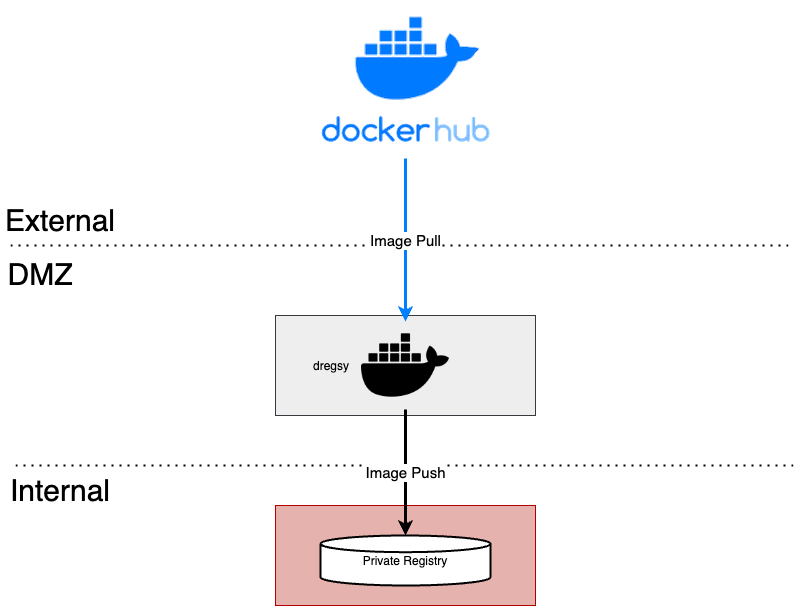
In an environment situated between an external network and an internal network, dregsy is executed.
This tool periodically pulls specific container images from Dockerhub and uploads them to the organization's private container registry.
NOTE:
The dregsy tool described in this guide always pulls container images from Dockerhub, regardless of whether the images already exist in the destination registry.
And, Docker Hub limits the number of Docker image downloads, or pulls based on the account type of the user pulling the image
- For anonymous users, the rate limit is set to 100 pulls per 6 hours per IP address
- For authenticated users, it’s 200 pulls per 6 hour period.
- Users with a paid Docker subscription get up to 5000 pulls per day.
Install and Configuration
NOTE:
In this configuration, communication with Dockerhub is required, so it should be performed in an environment with internet access.
Also, this explanation is based on the installation of Cloudforet version 1.11.x
Prerequisite
- docker (Install Docker Engine)
Installation
Since the tools are executed using Docker, there is no separate installation process required.
The plan is to pull and run the dregsy image, which includes skopeo (mirror tool).
Configuration
- Create files
touch /path/to/your/dregsy-spaceone-core.yaml
touch /path/to/your/dregsy-spaceone-plugin.yaml
- Add configuration (dregsy-spaceone-core.yaml)
If authentication to the registry is configured with
username:password,
the information is encoded and set in the 'auth' field as shown below (example - lines 19 and 22 of the configuration).echo '{"username": "...", "password": "..."}' | base64
In the case of Harbor, Robot Token is not supported for authentication.
Please authenticate by encoding the username:password
relay: skopeo
watch: true
skopeo:
binary: skopeo
certs-dir: /etc/skopeo/certs.d
lister:
maxItems: 100
cacheDuration: 2h
tasks:
- name: sync_spaceone_doc
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token} # replace to your dockerhub token
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/spacectl
to: your_registry_project/spaceone/spacectl # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/marketplace-assets
to: your_registry_project/spaceone/marketplace-assets # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/docs
to: your_registry_project/spaceone/docs # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: redis
to: your_registry_project/spaceone/redis # replace to your registry project & repository
tags:
- 'latest'
- from: mongo
to: your_registry_project/spaceone/mongo # replace to your registry project & repository
tags:
- 'latest'
- name: sync_spaceone_core
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token}
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/console
to: your_registry_project/spaceone/console # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/inventory
to: your_registry_project/spaceone/inventory # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/console-api
to: your_registry_project/spaceone/console-api # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/cost-analysis
to: your_registry_project/spaceone/cost-analysis # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/statistics
to: your_registry_project/spaceone/statistics # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/secret
to: your_registry_project/spaceone/secret # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/file-manager
to: your_registry_project/spaceone/file-manager # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/monitoring
to: your_registry_project/spaceone/monitoring # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/supervisor
to: your_registry_project/spaceone/supervisor # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/identity
to: your_registry_project/spaceone/identity # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/notification
to: your_registry_project/spaceone/notification # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/repository
to: your_registry_project/spaceone/repository # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/plugin
to: your_registry_project/spaceone/plugin # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/config
to: your_registry_project/spaceone/config # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/console-api-v2
to: your_registry_project/spaceone/console-api-v2 # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/board
to: your_registry_project/spaceone/board # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/dashboard
to: your_registry_project/spaceone/dashboard # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- Add configuration (dregsy-spaceone-plugin.yaml)
relay: skopeo
watch: true
skopeo:
binary: skopeo
certs-dir: /etc/skopeo/certs.d
lister:
maxItems: 100
cacheDuration: 2h
tasks:
- name: sync_spaceone_plugin
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token} # replace to your dockerhub token
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/plugin-google-cloud-inven-collector
to: your_registry_project/spaceone/plugin-google-cloud-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-inven-collector
to: your_registry_project/spaceone/plugin-azure-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloudwatch-mon-datasource
to: your_registry_project/spaceone/plugin-aws-cloudwatch-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-activity-log-mon-datasource
to: your_registry_project/spaceone/plugin-azure-activity-log-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloudtrail-mon-datasource
to: your_registry_project/spaceone/plugin-aws-cloudtrail-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-ec2-inven-collector
to: your_registry_project/spaceone/plugin-aws-ec2-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-sns-mon-webhook
to: your_registry_project/spaceone/plugin-aws-sns-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-trusted-advisor-inven-collector
to: your_registry_project/spaceone/plugin-aws-trusted-advisor-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-monitor-mon-datasource
to: your_registry_project/spaceone/plugin-azure-monitor-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-email-noti-protocol
to: your_registry_project/spaceone/plugin-email-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-stackdriver-mon-datasource
to: your_registry_project/spaceone/plugin-google-stackdriver-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-telegram-noti-protocol
to: your_registry_project/spaceone/plugin-telegram-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-keycloak-identity-auth
to: your_registry_project/spaceone/plugin-keycloak-identity-auth # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-prometheus-mon-webhook
to: your_registry_project/spaceone/plugin-prometheus-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-slack-noti-protocol
to: your_registry_project/spaceone/plugin-slack-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-grafana-mon-webhook
to: your_registry_project/spaceone/plugin-grafana-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloud-service-inven-collector
to: your_registry_project/spaceone/plugin-aws-cloud-service-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-phd-inven-collector
to: your_registry_project/spaceone/plugin-aws-phd-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-api-direct-mon-webhook
to: your_registry_project/spaceone/plugin-api-direct-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-cost-mgmt-cost-datasource
to: your_registry_project/spaceone/plugin-azure-cost-mgmt-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cost-explorer-cost-datasource
to: your_registry_project/spaceone/plugin-aws-cost-explorer-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-ms-teams-noti-protocol
to: your_registry_project/spaceone/plugin-ms-teams-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-monitoring-mon-webhook
to: your_registry_project/spaceone/plugin-google-monitoring-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-http-file-cost-datasource
to: your_registry_project/spaceone/plugin-http-file-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-cloud-log-mon-datasource
to: your_registry_project/spaceone/plugin-google-cloud-log-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
Run
No need to pull docker images separately.
The command below will get the image if there is no image locally
docker run -d --rm --name dregsy_spaceone_core -v /path/to/your/dregsy-spaceone-core.yaml:/config.yaml xelalex/dregsy:0.5.0
docker run -d --rm --name dregsy_spaceone_plugin -v /path/to/your/dregsy-spaceone-plugin.yaml:/config.yaml xelalex/dregsy:0.5.0
Management
- view log
docker logs -f {container_id|container_name}
- delete docker container
docker rm {container_id|container_name} [-f]
6 - Advanced configuration guide
Title and Favicon
Cloudforet has default title and CI with Wanny favicon.
![]()
But you can change them to your own title and favicon.
![]()
| Component | File Path | Description |
|---|---|---|
| Title | /var/www/title.txt | name of Title |
| Favicon | /var/www/favicon.ico | favicon file |
Console supports the functionality of changing title and favicon. The default values are in source code, but you can overwrite them when deploying pods.
NOTE: Both Title and Favicon should be exist together, even though you want to configure one of them!
This is an example value of console.yaml file.console:
production_json:
DOMAIN_NAME_REF: hostname
CONSOLE_API:
ENDPOINT: https://console-v1.api.example.com
CONSOLE_API_V2:
ENDPOINT: https://console-v2.api.example.com
DOMAIN_IMAGE:
CI_LOGO: https://raw.githubusercontent.com/cloudforet-io/artwork/main/logo/symbol/Cloudforet_symbol--dark-navy.svg
CI_TEXT_WITH_TYPE: https://raw.githubusercontent.com/kren-ucloud/artwork/main/logo/KREN-logo.png
SIGN_IN: https://raw.githubusercontent.com/cloudforet-io/artwork/main/illustrations/happy-new-year-2024.png
CI_TEXT: https://raw.githubusercontent.com/cloudforet-io/artwork/main/logo/wordmark/Cloudforet_wordmark--primary.svg
volumeMounts:
application:
- name: favicon
mountPath: /var/www/title.txt
subPath: title.txt
readOnly: true
- name: favicon-img
mountPath: /var/www/favicon.ico
subPath: favicon.ico
readOnly: true
volumes:
- name: favicon
configMap:
name: favicon
- name: favicon-img
configMap:
name: favicon-img
- name: timezone
hostPath:
path: /usr/share/zoneinfo/Asia/Seoul
- name: log-volume
emptyDir: {}
The actual values are from Kubernetes ConfigMap object. So you might have to change the value at ConfigMap or create a new one and mount it in your pod.
Title(title.yaml)
apiVersion: v1
kind: ConfigMap
metadata:
name: favicon
namespace: spaceone
data:
title.txt: |
KREN UCLOUD
Apply at your Kubernetes cluster.
kubectl apply -f title.yaml -n spaceone
Favicon (favicon.yaml)
Cloudforet new Favicon file is favicon.yaml
apiVersion: v1
kind: ConfigMap
metadata:
name: favicon-img
namespace: spaceone
binaryData:
favicon.ico: AAABAAEAAAAAAAEAIADxxxxxxx...
NOTE: favicon.ico must be base64 encoded.
# prepare your favicon.ico file, and encode it to base64 (shell command)
cat favicon.ico | base64
Apply at your Kubernetes cluster.
kubectl apply -f favicon.yaml -n spaceone
Corporate Identity
When you open Cloudforet page, you can see the default Cloudforet CI, logo and text. You can change the default Cloudforet CI with your company CI.
Login Page

Every Page

Update helm value of console (console -> production_json -> DOMAIN_IMAGE)
keyword: DOMAIN_IMAGE
| Configuration | Description | Format |
|---|---|---|
| CI_LOGO | Custom Logo Image | Image (56 * 56 px) |
| CI_TEXT_WITH_TYPE | CI Text Image | Image (164 * 40 px) |
| SIGN_IN | Sign-in page Image | Image (1024 * 1024 px) |
| CI_TEXT | CI Text Image On every page | Image (123 * 16 px) |
NOTE: Recommended file format is SVG. But if you would like to use a PNG file, use transparent background and double the size than recommended size.
NOTE: Cloudforet does not support uploading files, so upload CI files at your web server or S3.!
console:
production_json:
DOMAIN_NAME_REF: hostname
CONSOLE_API:
ENDPOINT: https://console-v1.api.example.com
CONSOLE_API_V2:
ENDPOINT: https://console-v2.api.example.com
DOMAIN_IMAGE:
CI_LOGO: https://raw.githubusercontent.com/cloudforet-io/artwork/main/logo/symbol/Cloudforet_symbol--dark-navy.svg
CI_TEXT_WITH_TYPE: https://raw.githubusercontent.com/kren-ucloud/artwork/main/logo/KREN-logo.png
SIGN_IN: https://raw.githubusercontent.com/cloudforet-io/artwork/main/illustrations/happy-new-year-2024.png
CI_TEXT: https://raw.githubusercontent.com/cloudforet-io/artwork/main/logo/wordmark/Cloudforet_wordmark--primary.svg
volumeMounts:
application:
- name: favicon
mountPath: /var/www/title.txt
subPath: title.txt
readOnly: true
- name: favicon-img
mountPath: /var/www/favicon.ico
subPath: favicon.ico
readOnly: true
volumes:
- name: favicon
configMap:
name: favicon
- name: favicon-img
configMap:
name: favicon-img
- name: timezone
hostPath:
path: /usr/share/zoneinfo/Asia/Seoul
- name: log-volume
emptyDir: {}
Google Analytics
You can apply Google Analytics to Cloudforet Console by following the steps below.
Create accounts and properties
Log in to your Google account after accessing the Google Analytics site.
Click the Start Measurement button.

Enter your account name and click the Next button.

Enter a property name and click the Next button.
In the property name, enter the name of the url you want to track.

Click the Create button.

Click the Agree button after agreeing to the data processing terms.

Set up data streams
Choose Web as the platform for the data stream you want to collect.

Enter your Cloudforet Console website URL and stream name and click the Create Stream button.

Check the created stream information and copy the measurement ID.

Set up the Cloudforet Helm Chart
Paste the copied measurement ID as the value for the GTAG_ID key in the helm chart settings as shown below.
# frontend.yaml
console:
...
production_json:
...
GTAG_ID: {measurement ID}
...
7 - Create secret by exist cert
If a public or private certificate has already been issued, you can create a secret through the existing certificate. The following is how to create a secret using the certificate_secret.yaml file.
Create Secret from certificate_secret.yaml file
If the certificate is ready, edit the certificate_secert.yaml file. The file can be downloaded from the link below. In addition, the downloaded content is edited and used as follows. https://github.com/cloudforet-io/charts/blob/master/examples/ingress/on_premise/certificate_secret.yaml
cat <<EOF> certificate_secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: spaceone-tls
namespace: spaceone # Change the namespace
data:
tls.crt: base64 encoded cert # openssl base64 -in cert.pem -out cert.base64
tls.key: base64 encoded key # openssl base64 -in key.pem -out key.base64
type: kubernetes.io/tls
EOF
Apply the certificate_secret.yaml file to the spaceone namespace through the following command.
kubectl apply -f certificate_secret.yaml -n spaceone