1 - 플러그인 사설 인증서 설정
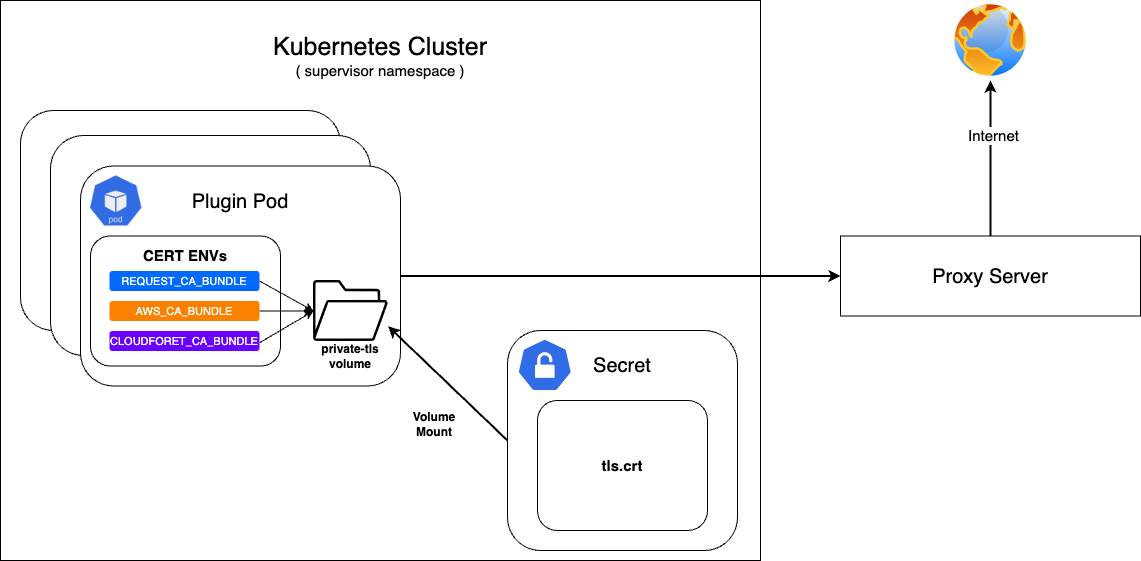
Cloudforet가 On-premise 환경에 구축될 경우 인터넷과 직접적인 통신이 되지 않고 Proxy 서버를 통해 접속이 될 수 있습니다.
이 때 Proxy 서버와의 통신 시 사설 인증서를 필요로 하게 됩니다.
먼저, 준비된 사설 인증서로 Secret으로 구성하고 이를 private-tls Volume에 Mount 합니다.
이후 supervisor의 KubernetesConnector에 인증서 설정에 필요한 여러 환경변수의 value가 private-tls volume의 tls.crt의 경로가 되도록 설정합니다.
준비된 사설 인증서를 Kubernetes Secret으로 등록
| Parameter | Description | Default |
|---|---|---|
| apiVersion | API version of resource | v1 |
| kind | Kind of resource | Secret |
| metadata | Metadata of resource | {...} |
| metadata.name | Name of resource | private-tls |
| metadata.namespace | Namespace of resource | spaceone |
| data | Data of resource | tls.crt |
| type | Type of resource | kubernetes.io/tls |
kubectl apply -f create_tls_secret.yml
---
apiVersion: v1
kind: Secret
metadata:
name: spaceone-tls
namespace: spaceone
data:
tls.crt: base64 encoded cert # openssl base64 -in cert.pem -out cert.base64
type: kubernetes.io/tls
KubernetesConnector에 설정
| Parameter | Description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor scheduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[] | Environment variables for plugin | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].name | Name of environment variable | REQUESTS_CA_BUNDLE, AWS_CA_BUNDLE, CLOUDFORET_CA_BUNDLE |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].value | Value of environment variable | /opt/ssl/cert/tls.crt |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[] | Volumes for plugin | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[].name | Name of volumes | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumes[].secret.secretName | Secret name of secret volume | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[] | Volume mounts of plugins | [...] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].name | Name of volume mounts | private-tls |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].mountPath | Path of volume mounts | /opt/ssl/cert/tls.crt |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.volumeMounts[].readOnly | Read permission on the mounted volume | true |
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
env:
- name: REQUESTS_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
- name: AWS_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
- name: CLOUDFORET_CA_BUNDLE
value: /opt/ssl/cert/tls.crt
volumes:
- name: private-tls
secret:
secretName: private-tls
volumeMounts:
- name: private-tls
mountPath: /opt/ssl/cert/tls.crt
readOnly: true
변경내용 반영
helm upgrade 및 pod 삭제 명령을 통해서 반영 할 수 있습니다.
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
2 - Change kubernetes namespace
K8S 환경에서 Cloudforet을 설치하게 되면 core 서비스는 spaceone, 확장 기능을 위한 plugin 서비스는 spaceone-plugin namespace에 설치됩니다. (v1.11.5 이하에서는 root-supervisor에 설치 됩니다.)
만약 사용자가 core 서비스나 plugin 서비스를 다른 이름의 namespace로 변경하고 싶거나, 단일 namespace에 설치하기를 희망한다면 옵션을 통해서 namespace를 변경해야 합니다.
namespace를 변경하기 위해서는 Cloudforet의 values.yaml에 변경 내용을 작성해야 합니다. 변경은 core서비스와 plugin 서비스를 각각 설정할 수 있습니다.
core 서비스의 namespace 변경
core 서비스의 namespace 변경을 위해서는 values.yaml 파일에서 global.namespace를 선언하여 spaceone-namespace 값을 추가합니다.
#console:
# production_json:
# CONSOLE_API:
# ENDPOINT: https://console.api.example.com # Change the endpoint
# CONSOLE_API_V2:
# ENDPOINT: https://console-v2.api.example.com # Change the endpoint
global:
namespace: spaceone-namespace # Change the namespace
shared_conf:
plugin 서비스의 namespace 변경
core 서비스 뿐만 아니라, supervisor의 plugin 서비스의 namespace도 변경할 수 있습니다. plugin 서비스는 supervisor에 의해 life-cycle이 관리되며 plugin의 namespace 설정도 supervisor에 설정합니다.
아래는 values.yaml 파일에서 plugin 서비스의 namespace를 변경히가 위해 supervisor를 설정한 부분입니다. supervisor.application_scheduler.CONNECTORS.KubernetesConnector.namespace에 plugin-namespace 값을 추가합니다.
#console:
supervisor:
application_scheduler:
HOSTNAME: spaceone.svc.cluster.local # Change the hostname
CONNECTORS:
KubernetesConnector:
namespace: plugin-namespace # Change the namespace
변경내용 반영
helm upgrade 및 pod 삭제 명령을 통해서 반영 할 수 있습니다.
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
3 - Kubernetes imagePullSecrets 설정
사용자들은 때때로 조직의 상황에 따라 Private Image를 관리하기 위해 Private 전용 Image Registry를 구축하고 그것을 이용합니다.
Private Image Registry로부터 Container Image를 가져오기 위해서는 자격 증명이 필요하고, Kubernetes에서는 Secret을 이용해 그러한 자격 증명을 Pod 등록하여 Private Container Image를 가져올때 사용할 수 있도록 할 수 있습니다.
자세한 내용은 공식 문서를 참고하세요.
자격증명을 위한 Secret 생성
Kubernetes pod는 kubernetes.io/dockerconfigjson 타입의 Secret을 이용해 Private Container Image를 가져올 수 있습니다.
이를 위해 registry 인증정보를 기반으로 자격 증명을 위한 secret을 생성합니다.
kubectl create secret docker-registry my-credential --docker-server=<your-registry-server> --docker-username=<your-name> --docker-password=<your-pword> --docker-email=<your-email>
자격증명 Secret을 Pod에 적용
Cloudforet의 helm chart value에 imagePullSecrets 을 명시하여 pod들이 자격 증명을 위한 secret을 mount하도록 할 수 있습니다.
WARN: kubernetes secret은 namespace scope의 resource이므로, 같은 namespace에 존재해야합니다.
Core service를 위한 imagePullSecrets 설정
| Parameter | description | Default |
|---|---|---|
| [services].imagePullSecrets[]] | imagePullSecrets configuration(* Each micro service section) | [] |
| [services].imagePullSecrets[].name | Name of secret type of kubernetes.io/dockerconfigjson | "" |
console:
enable: true
image:
name: spaceone/console
version: x.y.z
imagePullSecrets:
- name: my-credential
console-api:
enable: true
image:
name: spaceone/console-api
version: x.y.z
imagePullSecrets:
- name: my-credential
(이하 동일)
Plugin를 위한 imagePullSecrets 설정
| Parameter | description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor scheduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.imagePullSecrets[] | imagePullSecrets configuration for plugin | [] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.imagePullSecrets[].name | Name of secret type of kubernetes.io/dockerconfigjson for plugin | "" |
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
imagePullSecrets:
- name: my-credential
변경내용 반영
helm upgrade 및 pod 삭제 명령을 통해서 반영 할 수 있습니다.
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
4 - HTTP Proxy 설정
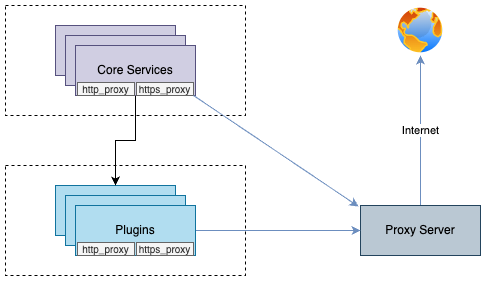
http_proxy https_proxy 환경변수 선언을 통해 pod들이 프록시 서버를 통해 외부로 통신할 수 있도록 할 수 있습니다.
이러한 설정은 각 Container의 환경변수에 http_proxy https_proxy를 선언하는 것으로 이루어집니다.
no_proxy 환경변수는 proxy 통신을 적용하지 않는 목적지에 대한 설정입니다.
cloudforet의 경우 Micro service간 통신을 위해 cluster 내부의 service 도메인은 제외하도록 설정하는 것을 추천합니다.
예제
Core service를 위한 proxy 설정
| Parameter | description | Default |
|---|---|---|
| global.common_env[] | Environment Variable for all micro services | [] |
| global.common_env[].name | Name of environment variable | "" |
| global.common_env[].value | Value of environment variable | "" |
global:
common_env:
- name: HTTP_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: HTTPS_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: no_proxy
value: .svc.cluster.local,localhost,{cluster_ip},board,config,console,console-api,console-api-v2,cost-analysis,dashboard,docs,file-manager,identity,inventory,marketplace-assets,monitoring,notification,plugin,repository,secret,statistics,supervisor
plugin을 위한 proxy 설정
| Parameter | description | Default |
|---|---|---|
| supervisor.application_scheduler | Configuration of supervisor schduler | {...} |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[] | Environment Variable for plugin | [] |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].name | Name of environment variable | "" |
| supervisor.application_scheduler.CONNECTORS.KubernetesConnector.env[].value | Name of environment variable | "" |
WRAN:
설치 환경에 따라 default local domain이 다른 경우가 있으니,.svc.cluster.local등의 default local domain을 자신의 환경에 맞게 변경해야합니다.
아래의 command로 현재 cluster의 dns 설정을 확인할 수 있습니다.kubectl run -it --rm busybox --image=busybox --restart=Never -- cat /etc/resolv.conf
supervisor:
enabled: true
image:
name: spaceone/supervisor
version: x.y.z
imagePullSecrets:
- name: my-credential
application_scheduler:
CONNECTORS:
KubernetesConnector:
env:
- name: HTTP_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: HTTPS_PROXY
value: http://{proxy_server_address}:{proxy_port}
- name: no_proxy
value: .svc.cluster.local,localhost,{cluster_ip},board,config,console,console-api,console-api-v2,cost-analysis,dashboard,docs,file-manager,identity,inventory,marketplace-assets,monitoring,notification,plugin,repository,secret,statistics,supervisor
변경내용 반영
helm upgrade 및 pod 삭제 명령을 통해서 반영 할 수 있습니다.
helm upgrade cloudforet cloudforet/spaceone -n spaceone -f values.yaml
kubectl delete po -n spaceone -l app.kubernetes.io/instance=cloudforet
5 - 프라이빗 이미지 저장소 지원
On-premise 환경을 운영하는 조직의 경우 보안상의 문제로
Internal Network에 자체 Container registry를 구축하여 운영하는 경우가 있습니다.
이러한 환경에 Cloudforet을 설치할 경우 외부 네트워크로의 접근이 제한되어,
Dockerhub에서 이미지를 가져와 자체 Container registry에 준비해두어야 할 필요가 있습니다.
Cloudforet은 이러한 상황에서 Container Image 동기화 작업을 자동화하기 위해 dregsy 라는
Container Registry Sync tool을 이용해 주기적으로 Container Image를 동기화하는 방법을 제안합니다.
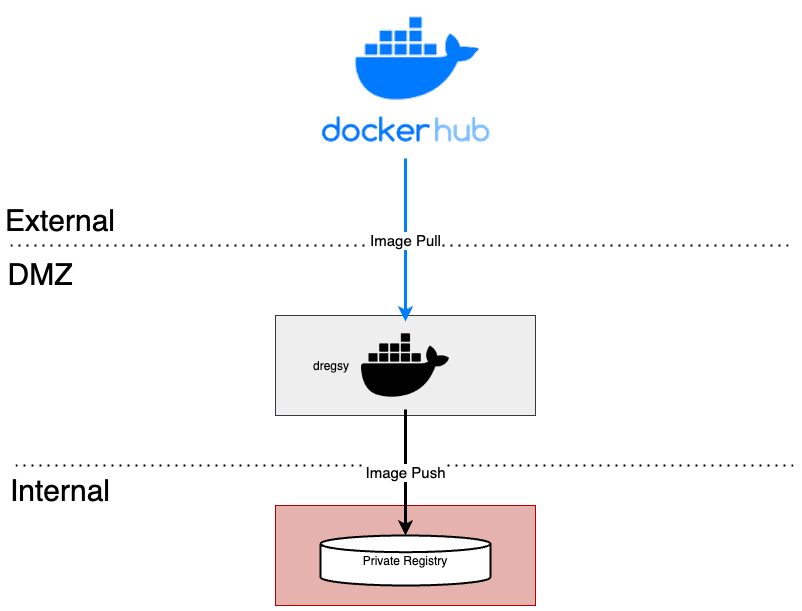
External Network와 Internal Network 사이에 위치한 환경에서 dregsy 를 실행합니다.
이것은 주기적으로 Dockerhub로부터 특정 Container Image를 가져와 자체 Container registry에 업로드합니다.
NOTE:
본 가이드에서 설명하고 있는 dregsy tool은 Container Image가 Destination Registry에
존재하는지의 여부와 관계없이 항상 Dockerhub로부터 Container image를 pull합니다.
Dockerhub의 rate limit은 아래와 같습니다. (Download rate limit)
- 익명 유저 100pulls per 6 hours
- 인증 유저 200pulls per 6 hours
- 구독 유저 5000pulls per day
설치 및 설정
NOTE:
본 구성의 경우, Dockerhub와 통신이 필요하기 때문에 외부 인터넷과 통신이 가능한 환경에서 이루어져야합니다.
또한, 1.11.x 버전의 Cloudforet 설치를 기준으로 설명합니다.
Prerequisite
- docker (Install Docker Engine)
Installation
Docker를 이용해 도구를 실행시키기 때문에 별도의 설치 과정은 필요하지 않음,
skopeo(mirror tool)을 포함한 dregsy image를 pull하여 실행할 예정.
Configuration
- 설정 파일 생성
touch /path/to/your/dregsy-spaceone-core.yaml
touch /path/to/your/dregsy-spaceone-plugin.yaml
- 설정 추가 (dregsy-spaceone-core.yaml)
만약, username:password 구성으로 Registry 인증을 하는 경우,
아래와 같이 정보를 encode하여 auth에 설정합니다. (예시 - 설정 19,22번째 라인)echo '{"username": "...", "password": "..."}' | base64
Harbor의 경우 Robot Token 인증은 지원이 어렵습니다. username:password를 encoding하여 인증해주세요.
relay: skopeo
watch: true
skopeo:
binary: skopeo
certs-dir: /etc/skopeo/certs.d
lister:
maxItems: 100
cacheDuration: 2h
tasks:
- name: sync_spaceone_doc
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token} # replace to your dockerhub token
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/spacectl
to: your_registry_project/spaceone/spacectl # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/marketplace-assets
to: your_registry_project/spaceone/marketplace-assets # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/docs
to: your_registry_project/spaceone/docs # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: redis
to: your_registry_project/spaceone/redis # replace to your registry project & repository
tags:
- 'latest'
- from: mongo
to: your_registry_project/spaceone/mongo # replace to your registry project & repository
tags:
- 'latest'
- name: sync_spaceone_core
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token}
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/console
to: your_registry_project/spaceone/console # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/inventory
to: your_registry_project/spaceone/inventory # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/console-api
to: your_registry_project/spaceone/console-api # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/cost-analysis
to: your_registry_project/spaceone/cost-analysis # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/statistics
to: your_registry_project/spaceone/statistics # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/secret
to: your_registry_project/spaceone/secret # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/file-manager
to: your_registry_project/spaceone/file-manager # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/monitoring
to: your_registry_project/spaceone/monitoring # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/supervisor
to: your_registry_project/spaceone/supervisor # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/identity
to: your_registry_project/spaceone/identity # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/notification
to: your_registry_project/spaceone/notification # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/repository
to: your_registry_project/spaceone/repository # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/plugin
to: your_registry_project/spaceone/plugin # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/config
to: your_registry_project/spaceone/config # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/console-api-v2
to: your_registry_project/spaceone/console-api-v2 # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/board
to: your_registry_project/spaceone/board # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- from: spaceone/dashboard
to: your_registry_project/spaceone/dashboard # replace to your registry project & repository
tags:
- 'regex: 1\.11\.(?:[0-9]?[0-9]).*'
- 설정 추가 (dregsy-spaceone-plugin.yaml)
relay: skopeo
watch: true
skopeo:
binary: skopeo
certs-dir: /etc/skopeo/certs.d
lister:
maxItems: 100
cacheDuration: 2h
tasks:
- name: sync_spaceone_plugin
interval: 21600 # 6 hours
verbose: true
source:
registry: registry.hub.docker.com
auth: {Token} # replace to your dockerhub token
target:
registry: {registry_address} # replace to your registry address
auth: {Token} # replace to your registry token
skip-tls-verify: true
mappings:
- from: spaceone/plugin-google-cloud-inven-collector
to: your_registry_project/spaceone/plugin-google-cloud-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-inven-collector
to: your_registry_project/spaceone/plugin-azure-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloudwatch-mon-datasource
to: your_registry_project/spaceone/plugin-aws-cloudwatch-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-activity-log-mon-datasource
to: your_registry_project/spaceone/plugin-azure-activity-log-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloudtrail-mon-datasource
to: your_registry_project/spaceone/plugin-aws-cloudtrail-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-ec2-inven-collector
to: your_registry_project/spaceone/plugin-aws-ec2-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-sns-mon-webhook
to: your_registry_project/spaceone/plugin-aws-sns-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-trusted-advisor-inven-collector
to: your_registry_project/spaceone/plugin-aws-trusted-advisor-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-monitor-mon-datasource
to: your_registry_project/spaceone/plugin-azure-monitor-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-email-noti-protocol
to: your_registry_project/spaceone/plugin-email-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-stackdriver-mon-datasource
to: your_registry_project/spaceone/plugin-google-stackdriver-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-telegram-noti-protocol
to: your_registry_project/spaceone/plugin-telegram-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-keycloak-identity-auth
to: your_registry_project/spaceone/plugin-keycloak-identity-auth # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-prometheus-mon-webhook
to: your_registry_project/spaceone/plugin-prometheus-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-slack-noti-protocol
to: your_registry_project/spaceone/plugin-slack-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-grafana-mon-webhook
to: your_registry_project/spaceone/plugin-grafana-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cloud-service-inven-collector
to: your_registry_project/spaceone/plugin-aws-cloud-service-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-phd-inven-collector
to: your_registry_project/spaceone/plugin-aws-phd-inven-collector # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-api-direct-mon-webhook
to: your_registry_project/spaceone/plugin-api-direct-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-azure-cost-mgmt-cost-datasource
to: your_registry_project/spaceone/plugin-azure-cost-mgmt-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-aws-cost-explorer-cost-datasource
to: your_registry_project/spaceone/plugin-aws-cost-explorer-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-ms-teams-noti-protocol
to: your_registry_project/spaceone/plugin-ms-teams-noti-protocol # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-monitoring-mon-webhook
to: your_registry_project/spaceone/plugin-google-monitoring-mon-webhook # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-http-file-cost-datasource
to: your_registry_project/spaceone/plugin-http-file-cost-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
- from: spaceone/plugin-google-cloud-log-mon-datasource
to: your_registry_project/spaceone/plugin-google-cloud-log-mon-datasource # replace to your registry project & repository
tags:
- 'semver: >=1.0.0 <1.99.0'
- 'keep: latest 2'
Run
Docker image를 별도로 download 받을 필요가 없습니다.
아래의 command가 docker image를 확인 후 없다면 가져옵니다.
docker run -d --rm --name dregsy_spaceone_core -v /path/to/your/dregsy-spaceone-core.yaml:/config.yaml xelalex/dregsy:0.5.0
docker run -d --rm --name dregsy_spaceone_plugin -v /path/to/your/dregsy-spaceone-plugin.yaml:/config.yaml xelalex/dregsy:0.5.0
Management
- view log
docker logs -f {container_id|container_name}
- delete docker container
docker rm {container_id|container_name} [-f]
6 - 기존 인증서로 Secret 만들기
공인 혹은 사설 인증서를 이미 발급받은 경우에는 기존 인증서를 통해서 Secret을 생성 할 수 있습니다. 다음은 certificate_secret.yaml 파일을 이용하여 Secret을 생성하는 방법입니다.
Create Secret from certificate_secret.yaml file
기존에 발급받은 인증서가 준비 되었다면 certificate_secert.yaml 파일을 편집합니다. 해당 파일은 다음의 링크에서 다운로드 할 수 있습니다. 또한 다운로드받은 내용을 아래와 같이 편집하여 사용 합니다. https://github.com/cloudforet-io/charts/blob/master/examples/ingress/on_premise/certificate_secret.yaml
cat <<EOF> certificate_secret.yaml
apiVersion: v1
kind: Secret
metadata:
name: spaceone-tls
namespace: spaceone # Change the namespace
data:
tls.crt: base64 encoded cert # openssl base64 -in cert.pem -out cert.base64
tls.key: base64 encoded key # openssl base64 -in key.pem -out key.base64
type: kubernetes.io/tls
EOF
certificate_secret.yaml 파일을 다음 명령어를 통해서 spaceone namespace에 반영합니다.
kubectl apply -f certificate_secret.yaml -n spaceone